Social engineering encompasses a wide range of malicious activities conducted through human interactions. The attacker attempts to build rapport with the victim in an effort to elicit protected information or bypass security requirements. Social engineering, when done correctly, is an extremely effective way to obtain otherwise protected information from individuals. There are four steps to a successful social engineering attack.
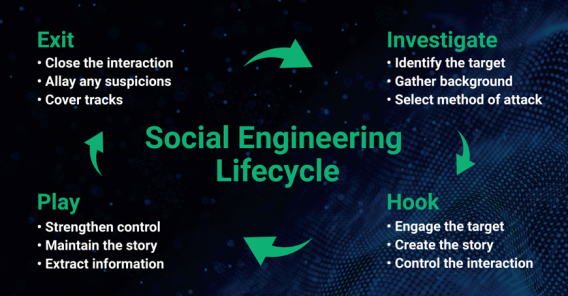
Step 1: Identify the target and conduct reconnaissance.
Step 2: Engage the target, usually via phone, develop relationship, build rapport, and obtain target’s trust.
Step 3: Continue with rapport building and elicit information, as victim trusts you, feels sorry for you, or wants to help you.
Step 4: Exploit victim and exit.
As effective as these attacks are, they will not work if employees follow their companies’ policies regarding the dissemination of protected information. Do not allow the caller to make you feel sorry for them!!




